
Decided to pursue the Certified Ethical Hacker Exam (CEHv12) but don’t know where to start. This blog post you need to read! The direction you should strive for is looking for the latest 312-50V12 dumps 2023.
Pass4itSure updates 312-50V12 dumps 2023 https://www.pass4itsure.com/312-50v12.html New exam question and answer questions pdf and software to help you pass the exam easily.
Be sure to check out the 312-50V12 exam tips and share some free 312-50V12 exam questions!
Passing your EC-COUNCIL 312-50V12 exam is easy!
If you work hard, the power is great. To pass the exam, you must first choose the right direction of effort, the wrong direction will be in vain.
Therefore, you should strive to use the Pass4itSure 312-50V12 dumps practice exam questions to pass the EC-COUNCIL 312-50V12 exam as soon as possible.
A large number of facts have proved that the dumps provided by Pass4itSure are more suitable for the exam, and the questions are all set around the real test content, real and valid.
Take some 312-50V12 online tests!
One of the best ways to learn about the Certified Ethical Hacker Exam (CEHv12) certification is to experience the online Practice Test learning materials. It is very necessary to do 312-50V12 practice questions, not only to promote the understanding of knowledge but also to experience the process of exams.
Latest 312-50V12 free dumps questions
New Question 1:
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
A. Converts passwords to uppercase.
B. Hashes are sent in clear text over the network.
C. Makes use of only 32-bit encryption.
D. Effective length is 7 characters.
Correct Answer: ABD
New Question 2:
Which type of attack attempts to overflow the content-addressable memory (CAM) table in an Ethernet switch?
A. Evil twin attack
B. DNS cache flooding
C. MAC flooding
D. DDoS attack
Correct Answer: C
New Question 3:
User A is writing a sensitive email message to user B outside the local network. User A has chosen to use PKI to secure his message and ensure only user B can read the sensitive email. At what layer of the OSI layer does the encryption and decryption of the message take place?
A. Application
B. Transport
C. Session
D. Presentation
Correct Answer: D
https://en.wikipedia.org/wiki/Presentation_layer
In the seven-layer OSI model of computer networking, the presentation layer is layer 6 and serves as the data translator for the network. It is sometimes called the syntax layer. The presentation layer is responsible for the formatting and delivery of information to the application layer for further processing or display.
Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.
New Question 4:
Study the following log extract and identify the attack.
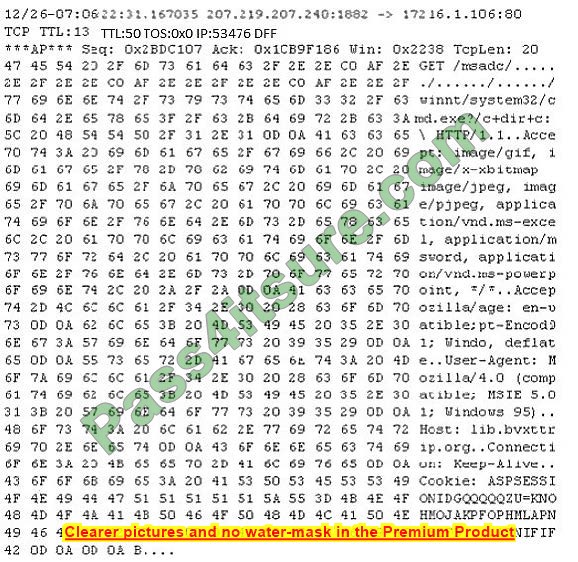
A. Hexcode Attack
B. Cross-Site Scripting
C. Multiple Domain Traversal Attack
D. Unicode Directory Traversal Attack
Correct Answer: D
New Question 5:
Which tool can be used to silently copy files from USB devices?
A. USB Grabber
B. USB Snoopy
C. USB Sniffer
D. Use Dumper
Correct Answer: D
New Question 6:
While browsing his Facebook teed, Matt sees a picture one of his friends posted with the caption. “Learn more about your friends!”, as well as a number of personal questions. Matt is suspicious and texts his friend, who confirms that he did indeed post it.
With the assurance that the post is legitimate. Matt responds to the questions on the post, a few days later. Mates’s bank account has been accessed, and the password has been changed. What most likely happened?
A. Matt inadvertently provided the answers to his security questions when responding to the post.
B. Matt\’s bank-account login information was brute-forced.
C. Matt Inadvertently provided his password when responding to the post.
D. Matt\’s computer was infected with a keylogger.
Correct Answer: A
New Question 7:
Dayn, an attacker, wanted to detect if any honeypots are installed in a target network. For this purpose, he used a time-based TCP fingerprinting method to validate the response to a normal computer and the response of a honeypot to a manual SYN request. Which of the following techniques is employed by Dayn to detect honeypots?
A. Detecting honeypots running on VMware
B. Detecting the presence of Honeyd honeypots
C. Detecting the presence of Snort_inline honeypots
D. Detecting the presence of Sebek-based honeypots
Correct Answer: C
New Question 8:
Bob was recently hired by a medical company after it experienced a major cybersecurity breach. Many patients are complaining that their personal medical records are fully exposed on the Internet and someone can find them with a simple Google search.
Bob\’s boss is very worried because of regulations that protect those data. Which of the following regulations is mostly violated?
A. HIPPA/PHl
B. Pll
C. PCIDSS
D. ISO 2002
Correct Answer: A
PHI stands for Protected Health info. The HIPAA Privacy Rule provides federal protections for private health info held by lined entities and provides patients an array of rights with regard to that info. under HIPAA phi is considered to be any identifiable health info that\’s used, maintained, stored, or transmitted by a HIPAA-covered entity?
A healthcare provider, a health plan or health insurer, or an aid clearinghouse. or a business associate of a HIPAA-covered entity, in relation to the availability of aid or payment for aid services.
It is not only past and current medical info that\’s considered a letter under HIPAA Rules but however also future info concerning medical conditions or physical and mental health related to the provision of care or payment for care. phi is health info of any kind, together with physical records, electronic records, or spoken info.
Therefore, the letter includes health records, medical histories, lab check results, and medical bills. basically, all health info is considered a letter once it includes individual identifiers.
New Question 9:
While scanning with Nmap, Patin found several hosts which have the IP ID of incremental sequences. He then decided to conduct: nmap -Pn -p- -si kiosk.adobe.com www.riaa.com. kiosk.adobe.com is the host with incremental IP ID sequence. What is the purpose of using “-si” with Nmap?
A. Conduct stealth scan
B. Conduct ICMP scan
C. Conduct IDLE scan
D. Conduct silent scan
Correct Answer: C
Once a suitable zombie has been found, performing a scan is easy. Simply specify the zombie hostname to the -sI option and Nmap does the rest. Example 5.19 shows an example of Ereet scanning the Recording Industry Association of America by bouncing an idle scan off an Adobe machine named Kiosk.
Example 5.19. An idle scan against the RIAA
# nmap -Pn -p- -sI kiosk.adobe.com www.riaa.com
Starting Nmap ( http://nmap.org ) Idlescan using zombie kiosk.adobe.com (192.150.13.111:80); Class: Incremental Nmap scan report for 208.225.90.120 (The 65522 ports scanned but not shown below are in state: closed)
Port State Service 21/tcp open ftp 25/tcp open smtp 80/tcp open http 111/tcp open sunrpc 135/tcp open loc-srv 443/tcp open https 1027/tcp open IIS 1030/tcp open iad1 2306/tcp open unknown 5631/tcp open pcanywheredata 7937/tcp open unknown 7938/tcp open unknown 36890/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 2594.47 seconds
https://nmap.org/book/idlescan.html
New Question 10:
A large mobile telephony and data network operator has a data center that houses network elements. These are essentially large computers running on Linux. The perimeter of the data center is secured with firewalls and IPS systems.
What is the best security policy concerning this setup?
A. Network elements must be hardened with user ids and strong passwords. Regular security tests and audits should be performed.
B. As long as physical access to the network elements is restricted, there is no need for additional measures.
C. There is no need for specific security measures on the network elements as long as firewalls and IPS systems exist.
D. The operator knows that attacks and downtime are inevitable and should have a backup site.
Correct Answer: A
New Question 11:
Which of the following allows attackers to draw a map or outline the target organization\’s network infrastructure to know about the actual environment that they are going to hack.
A. Enumeration
B. Vulnerability analysis
C. Malware analysis
D. Scanning networks
Correct Answer: D
New Question 12:
Which regulation defines security and privacy controls for Federal information systems and organizations?
A. HIPAA
B. EU Safe Harbor
C. PCI-DSS
D. NIST-800-53
Correct Answer: D
NIST Special Publication 800-53 provides a catalog of security and privacy controls for all U.S. federal information systems except those related to national security. It is published by the National Institute of Standards and Technology, which is a non-regulatory agency of the United States Department of Commerce.
NIST develops and issues standards, guidelines, and other publications to assist federal agencies in implementing the Federal Information Security Modernization Act of 2014 (FISMA) and to help with managing cost-effective programs to protect their information and information systems.
New Question 13:
Peter, a system administrator working at a reputed IT firm, decided to work from his home and log in remotely. Later, he anticipated that the remote connection could be exposed to session hijacking.
To curb this possibility, he implemented a technique that creates a safe and encrypted tunnel over a public network to securely send and receive sensitive information and prevent hackers from decrypting the data flow between the endpoints.
What is the technique followed by Peter to send files securely through a remote connection?
A. DMZ
B. SMB signing
C. VPN
D. Switch network
Correct Answer: C
New Question 14:
On performing a risk assessment, you need to determine the potential impacts when some of the critical business processes of the company interrupt its service.
What is the name of the process by which you can determine those critical businesses?
A. Emergency Plan Response (EPR)
B. Business Impact Analysis (BIA)
C. Risk Mitigation
D. Disaster Recovery Planning (DRP)
Correct Answer: B
New Question 15:
Under what conditions does a secondary name server request a zone transfer from a primary name server?
A. When a primary SOA is higher that a secondary SOA
B. When a secondary SOA is higher that a primary SOA
C. When a primary name server has had its service restarted
D. When a secondary name server has had its service restarted
E. When the TTL falls to zero
Correct Answer: A
Thanks for reading:
I hope this blog has helped you! Strive to be in the right direction and choose the right Pass4itSure 312-50V12 dumps to pass the Certified Ethical Hacker Exam (CEHv12) exam. The exam questions above are not enough, here, get the full 312-50V12 dumps questions.